Archive for the ‘new media’ category
Something Wrong is Nothing Wrong: Jodi.org
Enter a web address and the page loads. The internet sucks your time and then you die.
Enter jodi.org and the page unloads. The tame mundane space of the web browser could collapse or explode into a primitive, dada-esque video game, a eye-spinning array of ASCII, a virus of smaller browser spawn unfolding across your screen, or a deranged version of your desktop.
In the newest Motherboard video installment, we head to a recent show at Eyebeam gallery in New York to meet the obscure collective behind this strange, subversive and darkly comical code: a pair of soft-spoken artists named Joan Heemskerk and Dirk Paesmans. From their base in Holland and their untold number of web domains, video game modifications, .exe’s and Youtube pages, Jodi (“jo” + “di”) has for over a decade been evoking and exposing the confusion, mistrust, fear and excitement we bring to our life with computer screens. (See a list of their work at Wikipedia.)
Long before the internet was soaked in a glut of obsessive Flash-happy graphic designers, Jodi was using and abusing web languages to create more than a distinctive style. Taking their cursors off the “undo” button, they used accidental errors in HTML and other codes to turn our screens from mere repositories of data into funhouses, from virtual displays of art into works of art themselves. Like previous Motherboard subjects Alexei Shulgin and Cory Arcangel, Jodi’s been called net.art pioneers, but the only labels they like are the ones that come after http://. When they won the Webby award for art in 1999, Salon wrote that the ceremony was “punctuated by a punk-rock moment, when the subversive German [sic] artists of jodi.org knocked a cameraman aside and flung their Webby across the room.” They left behind the award’s most memorable five-word acceptance speech: “Ugly commercial sons of bitches.”
Their disturbing, glitch-prone work has turned Jodi into the enfants terribles of the internet and earned them reprobation from web authorities. Whether it’s malicious or sadistic, hilarious or silly, Jodi’s work shows the beauty and wonder in malfunction. “Do not adjust your internet,” you almost hear a voice whispering through the code. “There’s nothing wrong.”
http://motherboard.vice.com/2009/12/30/something-wrong-is-nothing-wrong-jodi-org
PressPausePlay
The digital revolution of the last decade has unleashed creativity and talent of people in an unprecedented way, unleashing unlimited creative opportunites.
But does democratized culture mean better art, film, music and literature or is true talent instead flooded and drowned in the vast digital ocean of mass culture? Is it cultural democracy or mediocrity?
This is the question addressed by PressPausePlay, a documentary film containing interviews with some of the world’s most influential creators of the digital era.
http://www.presspauseplay.com/
watch on VIMEO: http://vimeo.com/34608191
The Garden of Forking Paths by Jorge Luis Borges
Text: http://web.archive.org/web/20060528160418/http://courses.essex.ac.uk/lt/lt204/forking_paths.htm
Wiki: http://en.wikipedia.org/wiki/The_Garden_of_Forking_Paths
neural.it
 media art. hacktivism. emusic. since 1993.http://www.neural.it/
media art. hacktivism. emusic. since 1993.http://www.neural.it/
New Media at Merz Akademie
Interface Design BA program at Merz Akademie is a proper place to study web and interface design, spacial interaction and virtual reality, computational design, digital culture, new media arts. Studies are guided by Prof. Olia Lialina, pioneer of net art and new media researcher, and Prof. Mario Doulis, interface designer and VR expert.
Among our teachers are world famous theoreticians, designers, developers, musicians and artists: Johannes Auer, Roland Blach, Dragan Espenschied, Jana Frank, Alexander Goetz, Yun Chul Kim, Marius Watz, Guenter Wenzel and others.
Our graduates are known for being very special, because they can see over hypes and trends, they know how to master digital environments, they are innovative as designers and artists. The main purpose of this site is to present their works. Btw, our assistant, Joerg Frohnmayer, author of the most reasonable VR application in the world was a student of Merz Akademie as well.
This site is an attempt to combine a blog about the pathway’s life life and events with an archive of student works and semester projects.
This is pretty cool, Street Fighter diagram: http://nm.merz-akademie.de/~alexander.schlegel/SF2_Facts3
and this: http://streetfighter-diagram.6x.to/
GWEI - Google Will Eat Itself
We generate money by serving Google text advertisments on a network of hidden Websites. With this money we automatically buy Google shares. We buy Google via their own advertisment! Google eats itself - but in the end “we” own it!
By establishing this autocannibalistic model we deconstruct the new global advertisment mechanisms by rendering them into a surreal click-based economic model.
After this process we hand over the common ownership of “our” Google Shares to the GTTP Ltd. [Google To The People Public Company] which distributes them back to the users (clickers) / public.
Excerpt from
Entering the Machine and Leaving It Again: Poetics of Software in
Contemporary Art by Florian Cramer:
“A very recent example is “Google will eat itself” http://www.gwei.org [slide] by ubermorgen.com and Alessandro Ludovico. ubermorgen.com consists of former etoy member Hans Bernhard and Liz Haas, Alessandro Ludovico is well known in Italy as the founder and editor of Neural magazine. “Google will eat itself” is simple to explain: it is a website that runs ads via the Google “AdSense” program, i.e. embedded commercial text advertising provided by Google, but bought from other companies. Google pays website owners a small fee for every click on an ad link; “gwei.org” uses this money to buy Google shares. The idea is that Google will pay the site to get bought up by it. Ideally, gwei.org should make so much money from Google ad payments that it can buy up all Google shares. To accelerate this process, “Google will eat itself” imploys some hidden dirty programming hacks that trigger automatic clicks on the advertising so that any user who visits the site will click multiple Google ads at once.
It is not only one company eating up another, but also a piece of software eating up another software. Google is one of the first world companies that is a piece of online software, with search requests as its input, and a double output of search results and money to the shareholders. This collapsing of software program and corporation get turned against itself by gwei.org. It is the net.art of an Internet that is no longer an open field of experimentation, but a corporate space. The dark-humorous actionism of the piece manifests yet another resolution of the conflict that had originally voiced by Moles and Debord, technical formalism versus agency.”

Humorous and surprising, smart and provocative, Rethinking Curating: Art after New Media (MIT Press, 2010) jumps from opposing viewpoints to opposing personalities, from one arts trajectory to another. The entire book is a dialectic exercise: none of its problems or theories are solved or concluded, but are rather complicated through revelations around their origins, arguments and appropriations. Overall, the book adopts the collaborative style and hyperlinked approach of the media and practice it purports to rethink. In other words, it is not just the content of the book that asks us to rethink curating, but the reading itself; by the end, we are forced to digest and internalize the consistently problematized behaviors of the “media formerly known as new.”
Sarah Cook and Beryl Graham, co-editors of the CRUMB site and list (the Curatorial Resource for Upstart Media Bliss), have co-authored the book via email and on a Wiki, and assert outright that it is not a “theory book”; its structure instead “reflects the CRUMB approach to research, which discusses and analyzes the process of how things are done” (12). The sheer number of examples, citations, and first-person accounts in this nearly 350-page volume make it so that every time the trajectory coheres into a singular point or argument, it is then broken up again, into a constellation of ideas that make us rethink, again. We are issued challenge after challenge to our assumptions about media, our understandings of curatorial practice, and our opinions about the spaces in which we exhibit art. It is only after an exhaustive study of seemingly irreconcilable philosophies, practices and venues, the book implicitly argues, that we can begin to engage with what needs to be rethought, and how to do so.
Rethinking Curating makes three basic arguments. First, that one must approach a broad set of histories in trying to understand any given artwork, and “for new media art this set includes technological histories, which are essentially interdisciplinary and patchily documented” (283). Second, that such broad histories have led to the unique development of “critical vocabularies for the fluid and overlapping characteristics of new media art” (283). Cook and Graham reason that new media are best understood not as materials but as “behaviors” – participatory, performative or generative, for example. And third, that these behaviors demand a rethinking of curating, new modes of “looking at the production, exhibition, interpretation, and wider dissemination (including collection and conservation) of new media art” (1).
LUST: A Poster Wall for the 21st Century
On the occasion of the opening of the new Graphic Design Museum in Breda (NL) the posterwall for the 21st century was launched, both online and as an installation in the museum itself. In the museum 600 unique posters are automatically generated daily using content gathered from various internet sources. Online, one new poster is generated every five minutes. Constantly new and updated, the posters contain content covering a range of topics such as cultural events, news, weather, etc. In the museum it’s placed at the end of the overview exhibition ‘100 Years of Graphic Design in the Netherlands’. It attempts to provide insight into the direction graphic design might go in the future while posing the question: ‘Do we still need graphic designers?’
http://www.lust.nl/posterwall/
Auto-Tune the News
A bunch of guys use Auto-tune to remix the news to form music videos.
New Frontiers @ Sundance 2010
Just came back from Sundance, watched a bunch of great indie films but was so inspired to see the festival including a new direction: the intersection of film + art.
Touch My Body
Touch My Body is a conceptual miracle. Take Mariah Carey’s video, cut out every sound and image except for Maria and fill the rest with fluorescent green. Then publish it on YouTube and wait for the people to fill in the void. Insubordinate art for the masses, republished on his own site HERE. We curate a second chef-d’oeuvre by Laric: AIRCONDITION. You’ll love it.
http://www.unitedvloggers.com/2008/11/15/touch-my-body-green-screen-version/
Cory Arcangel’s Clouds
Super Mario Clouds» is based on the «Super Mario» game for Nintendo’s NES game console. Cory Arcangel hacked the game and modified it so that all that remains of the game are the white clouds on a blue sky. Gone is the main character, Super Mario, who the player had to guide through a labyrinth in the original jump and run game, just like the obstacles, landscapes and opponents that lend the game its narrative structure. Those people who are familiar with the game can imagine them on the empty background, everyone else will just see the cartoon-like display of a sky. The work was created on the basis of a manipulation of the hardware and software. Cory Arcangel had to open the cartridge, on which the game was stored, and replace the Nintendo graphics chip with a chip on which he had burned a program he had written himself. Cory Arcangel is a member of the Beige Programming Ensemble who have focused their artistic programme on the hacking ethic of manipulating existing technology, thereby taking the modification of legacy technology to absurd extremes: the group have published computer programs pressed on records and organise an annual competition for «cassette disk jockeys.»
Google: A New Approach to China
1/12/2010 03:00:00 PM
Like many other well-known organizations, we face cyber attacks of varying degrees on a regular basis. In mid-December, we detected a highly sophisticated and targeted attack on our corporate infrastructure originating from China that resulted in the theft of intellectual property from Google. However, it soon became clear that what at first appeared to be solely a security incident–albeit a significant one–was something quite different.
First, this attack was not just on Google. As part of our investigation we have discovered that at least twenty other large companies from a wide range of businesses–including the Internet, finance, technology, media and chemical sectors–have been similarly targeted. We are currently in the process of notifying those companies, and we are also working with the relevant U.S. authorities.
Second, we have evidence to suggest that a primary goal of the attackers was accessing the Gmail accounts of Chinese human rights activists. Based on our investigation to date we believe their attack did not achieve that objective. Only two Gmail accounts appear to have been accessed, and that activity was limited to account information (such as the date the account was created) and subject line, rather than the content of emails themselves.
Third, as part of this investigation but independent of the attack on Google, we have discovered that the accounts of dozens of U.S.-, China- and Europe-based Gmail users who are advocates of human rights in China appear to have been routinely accessed by third parties. These accounts have not been accessed through any security breach at Google, but most likely via phishing scams or malware placed on the users’ computers.
We have already used information gained from this attack to make infrastructure and architectural improvements that enhance security for Google and for our users. In terms of individual users, we would advise people to deploy reputable anti-virus and anti-spyware programs on their computers, to install patches for their operating systems and to update their web browsers. Always be cautious when clicking on links appearing in instant messages and emails, or when asked to share personal information like passwords online. You can read more here about our cyber-security recommendations. People wanting to learn more about these kinds of attacks can read this U.S. government report (PDF), Nart Villeneuve’s blog and this presentation on the GhostNet spying incident.
We have taken the unusual step of sharing information about these attacks with a broad audience not just because of the security and human rights implications of what we have unearthed, but also because this information goes to the heart of a much bigger global debate about freedom of speech. In the last two decades, China’s economic reform programs and its citizens’ entrepreneurial flair have lifted hundreds of millions of Chinese people out of poverty. Indeed, this great nation is at the heart of much economic progress and development in the world today.
We launched Google.cn in January 2006 in the belief that the benefits of increased access to information for people in China and a more open Internet outweighed our discomfort in agreeing to censor some results. At the time we made clear that “we will carefully monitor conditions in China, including new laws and other restrictions on our services. If we determine that we are unable to achieve the objectives outlined we will not hesitate to reconsider our approach to China.”
These attacks and the surveillance they have uncovered–combined with the attempts over the past year to further limit free speech on the web–have led us to conclude that we should review the feasibility of our business operations in China. We have decided we are no longer willing to continue censoring our results on Google.cn, and so over the next few weeks we will be discussing with the Chinese government the basis on which we could operate an unfiltered search engine within the law, if at all. We recognize that this may well mean having to shut down Google.cn, and potentially our offices in China.
The decision to review our business operations in China has been incredibly hard, and we know that it will have potentially far-reaching consequences. We want to make clear that this move was driven by our executives in the United States, without the knowledge or involvement of our employees in China who have worked incredibly hard to make Google.cn the success it is today. We are committed to working responsibly to resolve the very difficult issues raised.
http://googleblog.blogspot.com/2010/01/new-approach-to-china.html
Baidu: Hacking war breaks out between Iran and China

An unlikely cyberwar broke out yesterday when Iranian hackers attacked China’s leading search engine and Chinese counterparts retaliated against Iranian websites.
In the morning, people accessing the web page of Baidu, China’s largest internet search engine, found it was covered with a picture of the Iranian flag and other symbols and the words “Iranian Cyber Army”.
Not long after, a rallying cry for retaliation emerged in Chinese online discussion groups, blogs and bulletin boards.
In the afternoon, participants and cybersecurity experts started reporting that Chinese flags and nationalist slogans had appeared on websites registered in Iran.
On another website registered in Iran, Chinese hackers displayed a message saying: “Please tell your so-called Iranian Cyber Army: Don’t intrusion chinese website about The United States authorities to intervene the internal affairs of Iran’s response. This is a warning!”
http://www.ft.com/cms/s/0/0ed1d424-ffe2-11de-ad8c-00144feabdc0.html?catid=76&SID=google
Sunrise and Sunset
WHITNEY.ORG INTERNET ART PROJECT
http://whitney.org/Sunset
A series of Internet art projects commissioned by the Whitney specifically for whitney.org mark sunset and sunrise in New York City every day. Unfolding over a timeframe of ten to thirty seconds, each project accompanies a transition of the website’s background color from white (day) to black (night) and vice versa. A new project will be posted every three to four months.
Christiane Paul, the Whitney’s adjunct curator of new media, notes: “What distinguishes these projects is that they use whitney.org as their habitat, disrupting, replacing, or engaging with the museum website as an information environment. This form of engagement captures the core of artistic practice on the Internet, the intervention in existing online spaces.”
To see sunset or sunrise, be anywhere on this website. Sunset today: 4:39 PM, New York time. Sunrise: 6:41 AM. Time in New York now: 2:32:25 AM.
untitled landscape #5
First in the series of commissions is “Untitled Landscape #5,” a project by the collaborative ecoarttech, (Cary Peppermint and Christine Nadir). At sunrise and sunset, fluctuating orbs of light disrupt the “digital landscape,” and the information environment of whitney.org is disordered by ecoarttech’s visuals, suggesting a natural phenomenon. The size and speed of the orbs will vary based on the number of visitors to whitney.org since the previous sunrise (for sunset) or sunset (for sunrise); higher visitation results in larger, slower-moving orbs. ecoarttech’s work has consistently explored relationships between landscape, technology, and culture, and their commissioned work for whitney.org metaphorically explores the museum’s information landscape as it is shaped by its visitors.
live.burberry.com

For the first time, the 153 year old luxury fashion house Burberry will be streaming its show live from London Fashion Week at live.burberry.com. Viewers worldwide will be able to share their thoughts on the collection in real time as they watch the show.
The show signals the longest catwalk at LFW of 40m and the longest front row. This is also the first time the Parade Ground will be used to host a fashion show. The Burberry show space is within walking distance from the recently opened Burberry Global Headquarters at Horseferry house, designed by Christopher Bailey, Burberry Creative Director, where Christopher and Burberry CEO Angela Ahrendts will be hosting an event to mark the brand’s involvement in London Fashion Week following the show.
Dialtones: A Telesymphony
Dialtones (A Telesymphony) (2001-2002: Golan Levin, Gregory Shakar, Scott Gibbons, Yasmin Sohrawardy, Joris Gruber, Erich Semlak, Gunther Schmidl, Joerg Lehner, and Jonathan Feinberg) is a large-scale concert performance whose sounds are wholly produced through the carefully choreographed ringing of the audience’s own mobile phones. Before the concert, participants register their mobile phone numbers at a series of web terminals; in exchange, new ringtone melodies are automatically transmitted to their phones, and their seating assignment tickets are generated. During the concert, the audience’s phones are dialed up by live performers, using custom software which permits as many as 60 phones to ring simultaneously. Because the exact location and tone of each participant’s mobile phone is known in advance, the Dialtones concert is able to present a diverse range of unprecedented sonic phenomena and musically interesting structures, such as waves of polyphony which cascade across the audience. Dialtones was presented at the Ars Electronica Festival in September 2001, and at the Swiss National Exposition in May and June of 2002.
I Love Bees
I Love Bees (also known as ilovebees or ILB for short) was an alternate reality game (ARG) that served as both a real-world experience and viral marketing campaign for the release of developer Bungie’s 2004 video game Halo 2. The game was created by 42 Entertainment, who had previously created an ARG for the film A.I., and would later create Why So Serious? for the Warner Brothers film The Dark Knight. I Love Bees was commissioned by Microsoft, Halo 2’s publisher.I Love Bees was first advertised by a subliminal message in a Halo 2 trailer; players who investigated the titular website discovered that the pages appeared to be hacked by a mysterious intelligence. As players solved puzzles, audio logs were posted to the ilovebees.com site which gradually revealed more of the fictional back-story, involving a marooned artificial intelligence stranded on Earth and its attempts to put itself back together.I Love Bees was a marketing success; 250,000 people viewed the ilovebees website when it was launched in August 2004, and more than 500,000 returned to the site every time the pages were updated. More than three million visitors viewed the site over the course of three months, and thousands of people around the world participated in the game. I Love Bees won numerous awards for its innovation and helped spawn numerous other alternate reality games for video games.
Alternate reality games or ARGs are designed to involve fans of video games or other media in a form of viral marketing which CNET described as encompassing “real-life treasure hunting, interactive storytelling, video games and online [communities]”.[1] I Love Bees began when jars of honey were received in the mail by people who had previously participated in alternate reality games. The jars contained letters leading to the I Love Bees website and a countdown.[2] At around the same time, theatrical trailers for Halo 2 concluded with the Xbox logo and a URL, xbox.com, that quickly flashed a link to ilovebees.com,[3] ostensibly a hacked site related to beekeeping.[2]
Both events, not connected publicly for several weeks, caused the curious to visit the website ilovebees.com. The site, which appeared to be dedicated to honey sales and beekeeping, was covered in confusing random characters and sentence fragments. Dana, the ostensible webmaster of the ilovebees site, created a weblog stating that something had gone wrong with her website, and the site itself had been hacked.[4] Suspecting that this was a mystery that could be unraveled, Halo and ARG fans spread the link and began to work on figuring out what was going on.
Players respond to a phone call
The gameplay of I Love Bees tasked players around the world to work together to solve problems, with little or no direction or guidance.[5] For example, the game presented players with 210 pairs of global positioning system coordinates and time codes, with no indications to what the locations referred to.[5] Players eventually figured out the coordinates referred to pay phones and the times to when the phones would ring; one player in Florida stayed by a phone while Hurricane Frances was minutes away in order to recite answers to prerecorded questions.[6] Other phone calls were made by live persons known as “operators”; these calls allowed players to interact with the characters of the games in spontaneous and occasionally humorous ways.[7] Other players treated the corrupted data on ilovebees.com as encrypted files to decipher, or used image files found on the web server to solve puzzles.[6] After players completed certain tasks, they were rewarded with new installments to an audio drama which revealed the reasons for the ilovebees.com malfunction.[6]
Over time, the game’s mechanisms for contacting players grew more complex. Players were sent messages via email, called on their cell phones, and travelled to arranged meetings between players and characters.[8] The game culminated by inviting players of the game to visit one of four cinemas where they could get a chance to play Halo 2 before its release and collect a commemorative DVD.[9]
Social Networking Tools and our Future Society
In The Smooth and the Striated, Delueze and Guattari talk of the constant shift from striated space to smooth space and back. Neither space can exist on its own, and one continually sets the stage for the other to spring up from within it. A rational, gridded city as an example of the striated, will always have in it the smooth space of organic neighbourhood growth, community groups and homeless drifters. The internet first serving as a point-A-to-B information exchange route (point-to-point movement being a characteristic of striated space as opposed to smooth space where points do not terminate a path), became a space for people to become producers, creating and sharing new information, activities and ideologies—Benjamin’s description of the ideal production apparatus in the hands of the proletariat. However, as prescribed of organic and planned forces intermingling, the smooth space of the internet has bred a new striated space of ’social networking tools’, tools which threaten the act of production.
With “social networking tools”, such as facebook, we have stopped communicating directly with each other and instead ‘update’ our ’status’ via ‘wall posts’. We do not personally invite our friends with a phone call or email, but create an ‘event’ in the confines of the ’social networking tool’ which our network of real-life friends may not learn of if they are not a part of that insular network. We don’t express grief or even news of losing a grandparent other than by creating a status update that you are ‘going to a funeral’. The empathic connections between members of a society are cut, and without the feelings of kinship, care, respect, etc. the human connections in a society are severed and social responsibilities to each other are lost.
http://spacecollective.org/Xrene/4463/Social-Networking-Tools-and-our-Future-Society
Jan Chipchase: Future Perfect
Future Perfect is about the collision of people, society and technology, drawing on issues related to the design research that I conduct in part, on behalf of my employer - Nokia.
The New York Times has a decent write-up of this research here, related media here.
I currently conduct research for Nokia Design and split my time between running user studies and developing new applications, services and products that, if I do my job right, you’ll be using 3 to 15 years from now. Prior to this role I worked as Principal Researcher in the Nokia Research Center, Tokyo. I specialize in taking teams of concept/industrial designers, psychologists, usability experts, sociologists, and ethnographers into the field and, after a fair bit of work, getting them home safely. The tough part of the job is in using the data to inform, inspire and affect how my colleagues think and what they do, and in turning research into core intellectual property that underpins the future business. Since March 2009 I live and work from Los Angeles - with stints in London, Berlin and for the last 9 years, Tokyo.
China Channel Firefox Add-on
Experience the censored Chinese internet at home!
The Firefox add-on China Channel offers internet user outside China to surf the web as if they were in China. Take an unforgetable virtual trip to China and experience the technical expertise of the Chinese Ministry of Information Industry (supported by western companies). It’s open source, free and easy.
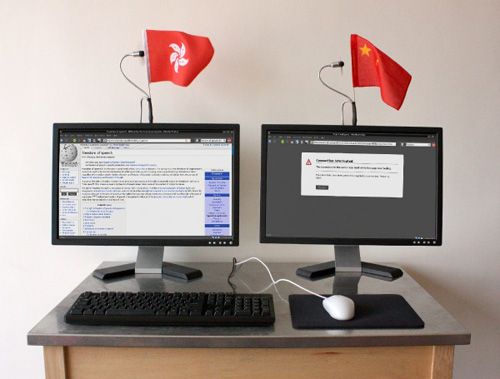
A gallery implementation of the China Channel Add-On
The installation has been on show at the group exhibition “SECOND LIFE” at Videtage Hong Kong 6.10.-4.11.2008Web 2.0 is a gallery installation consisting of two internet enabled computers, a hacked mouse and keyboard, and a custom plugin for the popular (and free) Firefox web browser. Two computers are connected to a single keyboard and mouse allowing visitors to control both identical machines at the same time while using just a single input device. The only difference between the two internet terminals is their network connection; one machine is connected to the less restricted internet in Hong Kong, while the other is connected to the internet through a connection point in the mainland of China.Unlike many tools which enable Chinese people to freely surf the web via connections to computers outside of China, this plugin routes all internet traffic to computers on the inside of the Chinese firewall, allowing web surfers to experience an Internet identical to that of Chinese.
Copyright © _dreams. All rights reserved.